In Snort version 2.9.7, Cisco will release a new dynamic preprocessor OpenAppID, which will add application identification to Snort capabilities. Application identification can be used to view how applications are using network resources and to enforce application aware rules to control and manage applications running on network.
Cisco will release open source code for hundreds of application detectors that can be used to identify frequently used applications. Users are free to copy and modify Cisco-provided detectors and create new detectors. The detectors will be small Lua programs that use a C-Lua API to interact with OpenAppID preprocessor. So far, OpenAppId support Up to 4 apps identified in each session.
Detector Code Structure
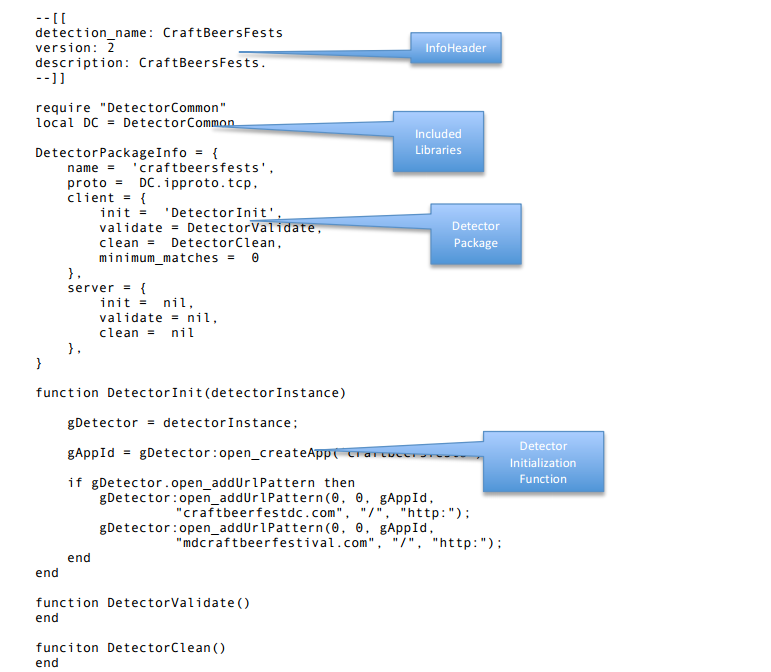
A detector has the following main components. The Detector Info Header, the included required libraries, the DetectorPackageInfo, the DetectorInit function, the DetectorValidator function, and the DetectorClean. We will describe each of them in more details below.
Rule Example
So you can Writing Snorts Rules to detect App:
- alert tcp any any -> any any(msg: "Get Back to Work";
- appid: facebook reddit;
- sid:1000000;
- rev:1)
Here we will go through a simple example on how to write a lua script to detect "CircleCityCon.com"!
Port
Besides the lua script, the simplest way to identify app is using port information (List of TCP/UDP port number). Below is one of the example:
-
- name: finger
- service_name: finger
- protocol: tcp/udp
- ports: 79
- appId: 637
Lua Script
Another approach is to write lua script to capture the symptom of traffic. First thing is to defined the header:
- require "DetectorCommon"
- local DC = DetectorCommon
- DetectorPackageInfo = {
- name = "circleCity",
- proto = DC.ipproto.tcp,
- client = {
- init = 'DetectorInit',
- clean = nil,
- validate = nil,
- minimum_matches = 0
- },
- server = {
- init = nil,
- validate = nil,
- clean = nil
- },
- }
The DetectorPackageInfo structure is required in each detector. It identifies client and server functions that will be called to initialize, validate (process packets) and cleanup the detector. OpenAppID preprocessor reads this structure after loading Lua code and calls initialization functions.
The structure has the following elements:
* DetectorPackageInfo.name: This is a name for the detector that is used for logging purpose.
* DetectorPackageInfo.proto: Protocol value. It can be DC.ipproto.tcp or DC.ipproto.udp.
* DetectorPackageInfo.client: If the detector identifies client side application (for example Firefox) then this structure is populated. Detectors for payload application (example Facebook) will provide client section only. The following functions can be provided:
* DetectorPackageInfo.server: If the detector identifies a server side application (for example Apache web server) then this structure is populated. The structure provides init, validate and clean function names that have same purpose as in client side.
Each detector must have an initializer function that is present in the DetectorPackageInfo structure. OpenAppID preprocessor will call this function directly upon loading the detector. The function is given detectorInstance, an instance of Detector class, which should be stored globally and used for calling all Lua-C API functions. The function may perform one or more of the following:
So for our customized detector for "circlecitycon.com", we prepare below three AppId inside DetectorInit():
- function DetectorInit(detectorInstance)
- gDetector = detectorInstance
- gAppId = gDetector:open_createApp('CrcCtyCon');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"circlecitycon.com", "/", "http:");
- end
- gAppId = gDetector:open_createApp('CrcCtyConSched');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"circlecitycon.com", "/talks/schedule", "http:");
- end
- gAppId = gDetector:open_createApp('CrcCtyConTix');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"brownpapertickets.com", "/event/505248", "http:");
- end
- end
- void open_addUrlPattern(serviceAppId, clientAppId, payloadAppId, hostpattern, pathPattern, schemePattern) :
- int open_createApp(appName) :
So our entire lua script to detect "circlecitycon.com" is named circlecity.lua :
- circlecity.lua
- require "DetectorCommon"
- local DC = DetectorCommon
- DetectorPackageInfo = {
- name = "circleCity",
- proto = DC.ipproto.tcp,
- client = {
- init = 'DetectorInit',
- clean = nil,
- validate = nil,
- minimum_matches = 0
- },
- server = {
- init = nil,
- validate = nil,
- clean = nil
- },
- }
- function DetectorInit(detectorInstance)
- gDetector = detectorInstance
- gAppId = gDetector:open_createApp('CrcCtyCon');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"circlecitycon.com", "/", "http:");
- end
- gAppId = gDetector:open_createApp('CrcCtyConSched');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"circlecitycon.com", "/talks/schedule", "http:");
- end
- gAppId = gDetector:open_createApp('CrcCtyConTix');
- if gDetector.open_addUrlPattern then
- gDetector:open_addUrlPattern(0,0,gAppId,"brownpapertickets.com", "/event/505248", "http:");
- end
- end
- function DetectorValidate()
- end
So we have our lua script circlecity.lua to detect "circlecitycon.com". First thing first, let's put this lua script under path
Then try to open browser and key-in "circlecitycon.com":

And click on the top menu: Talks->Schedule:

Finally, click on the link "Buy Tickets Here" in the right side:
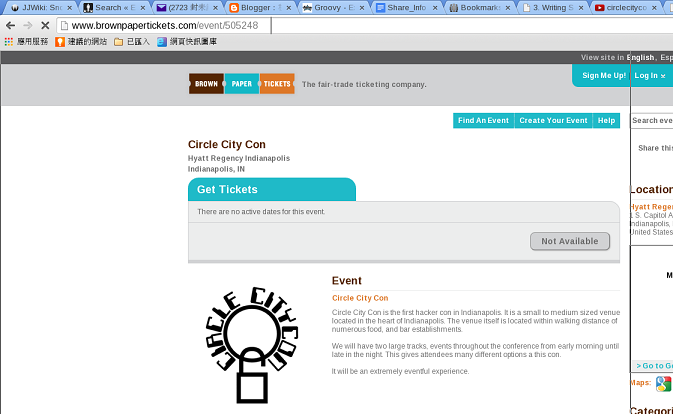
And wait for while until you see the log message look like below appear in the terminal running snort:
We can use command u2openappid to read the log file /var/log/snort/appstats-unified.log.1414568940 or use another simple useful shell chkAppidLog.sh to do it for us:
Or
Reference
* OpenDetectorDeveloperGuide.pdf
* Youtube - circlecitycon 114 openappid open source ...irewall with snort adam hogan
* Snort User Manual 2.9.6



沒有留言:
張貼留言