Preface
nmap is short for Network Mapper. It is an open source security tool for network exploration, security scanning and auditing. However, nmap command comes with lots of options that can make the utility more robust and difficult to follow for new users.
The purpose of this post is to introduce a user to the nmap command line tool to scan a host and/or network, so to find out the possible vulnerable points in the hosts. You will also learn how to use Nmap for offensive and defensive purposes.
More about nmap
From the man page:
It was originally written by Gordon Lyon and it can answer the following questions easily:
Sample setup (LAB)
Port scanning may be illegal in some jurisdictions. So setup a lab as follows:

Where,
How do I install nmap?
See:
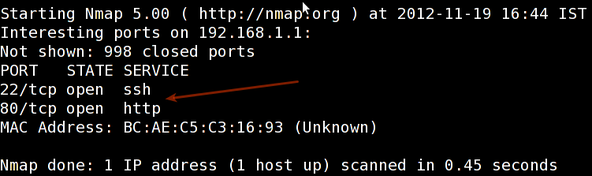
Scan a single host or an IP address (IPv4)
Sample outputs:
Scan multiple IP address or subnet (IPv4)
You can scan a range of IP address too:
You can scan a range of IP address using a wildcard:
Finally, you scan an entire subnet:
Read list of hosts/networks from a file (IPv4)
The -iL option allows you to read the list of target systems using a text file. This is useful to scan a large number of hosts/networks. Create a text file as follows:
- /tmp/test.txt
- server1.cyberciti.biz
- 192.168.1.0/24
- 192.168.1.1/24
- 10.1.2.3
- localhost
Excluding hosts/networks (IPv4)
When scanning a large number of hosts/networks you can exclude hosts from a scan:
OR exclude list from a file called /tmp/exclude.txt
Turn on OS and version detection scanning script (IPv4)
Find out if a host/network is protected by a firewall
Scan a host when protected by the firewall
Scan an IPv6 host/address
The -6 option enable IPv6 scanning. The syntax is:
Scan a network and find out which servers and devices are up and running
This is known as host discovery or ping scan:
How do I perform a fast scan?
Display the reason a port is in a particular state
Only show open (or possibly open) ports
Show all packets sent and received
Show host interfaces and routes
This is useful for debugging (ip command or route command or netstat command like output using nmap)
Sample outputs:

How do I scan specific ports?
Sample outputs:

The fastest way to scan all your devices/computers for open ports ever
How do I detect remote operating system?
You can identify a remote host apps and OS using the -O option:
See also: Fingerprinting a web-server and a dns server command line tools for more information.
How do I detect remote services (server / daemon) version numbers?
Scan a host using TCP ACK (PA) and TCP Syn (PS) ping
If firewall is blocking standard ICMP pings, try the following host discovery methods:
Scan a host using IP protocol ping
Scan a host using UDP ping
This scan bypasses firewalls and filters that only screen TCP:
Find out the most commonly used TCP ports using TCP SYN Scan
Scan a host for UDP services (UDP scan)
Most popular services on the Internet run over the TCP protocol. DNS, SNMP, and DHCP are three of the most common UDP services. Use the following syntax to find out UDP services:
Scan for IP protocol
This type of scan allows you to determine which IP protocols (TCP, ICMP, IGMP, etc.) are supported by target machines:
Scan a firewall for security weakness
The following scan types exploit a subtle loophole in the TCP and good for testing security of common attacks:
See how to block Xmas packkets, syn-floods and other conman attacks with iptables.
Scan a firewall for packets fragments
The -f option causes the requested scan (including ping scans) to use tiny fragmented IP packets. The idea is to split up the TCP header over several packets to make it harder for packet filters, intrusion detection systems, and other annoyances to detect what you are doing.
Cloak a scan with decoys
The -D option it appear to the remote host that the host(s) you specify as decoys are scanning the target network too. Thus their IDS might report 5-10 port scans from unique IP addresses, but they won't know which IP was scanning them and which were innocent decoys:
Scan a firewall for MAC address spoofing
How do I save output to a text file?
The syntax is:
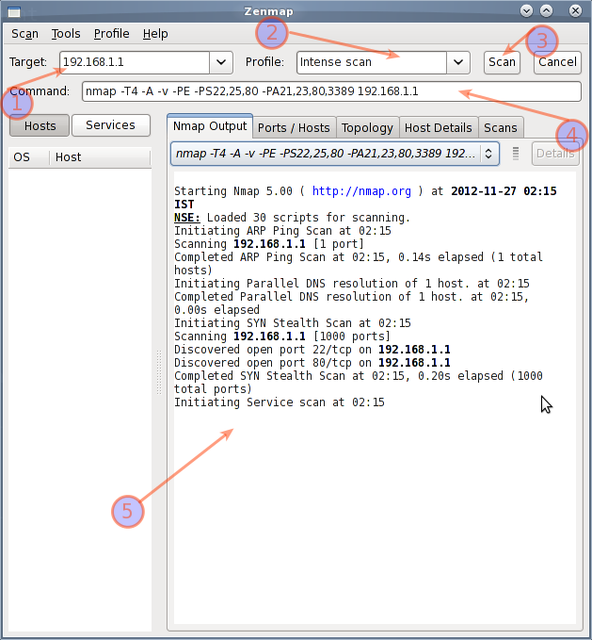
Not a fan of command line tools?
Try zenmap the official network mapper front end:
You can install zenmap using the following apt-get command:
How do I detect and block port scanning?
Try the following resources:
Supplement
* The official Nmap project guide to network discovery and security Scanning.
* The official Nmap project home page.

沒有留言:
張貼留言